White Paper
 Introduction
Introduction

1.Purpose of the White Paper
RICOH360 is our cloud service that enables more efficient business by digitally informing a 360-degree space.
The purpose of this document is to provide an overview of the security policy and processes for the cloud services used as the foundation for the provision of RICOH360, and to make a public announcement in accordance with the requirements of ISO/IEC 27017, the ISMS cloud security certification.
White Paper Subject
- For those who are considering introducing RICOH360
- For current RICOH360 users
 Third Party Certification
Third Party Certification

1.ISO/IEC27001
1.ISO/IEC27001
Our organization has acquired ISO/IEC27001/27017, the international standard for ISMS (Information Security Management System), on 28 May 2024, with the following scope of certification:
・Smart Vision Business Center, Ricoh Futures BU, Ricoh Company, Ltd.
Address: 1-3-6 Nakamagome, Ota-ku, Tokyo
「The provision of cloud services for 360-degree spherical images and videos in the smart vision business」
「The ISMS cloud security management system for the provision of system development, operation and maintenance of RICOH360 services (Cloud, apps, Tours) as a cloud service provider and for the use as a cloud service customer of Amazon Web Services, Vercel, MongoDB and imgix」

2.Information Security Policy for Cloud Computing
We take measures to protect our users' information assets in the cloud computing environment from information security threats and provide secure services that our users can use with peace of mind.
Information Security Policy for Cloud Computing
We take measures to protect our users' information assets in the cloud computing environment from information security threats and provide secure services that our users can use with peace of mind.
Our 'Information Security Policy' can be viewed at the following URL
https://www.ricoh360.com/security/
3.Information Security Organization
We have appointed a Chief Information Security Officer and given him or her overall responsibility and authority for information security. We have also established an Information Security Committee to operate and continuously improve our information security management system.
 Organizational Control Measures
Organizational Control Measures

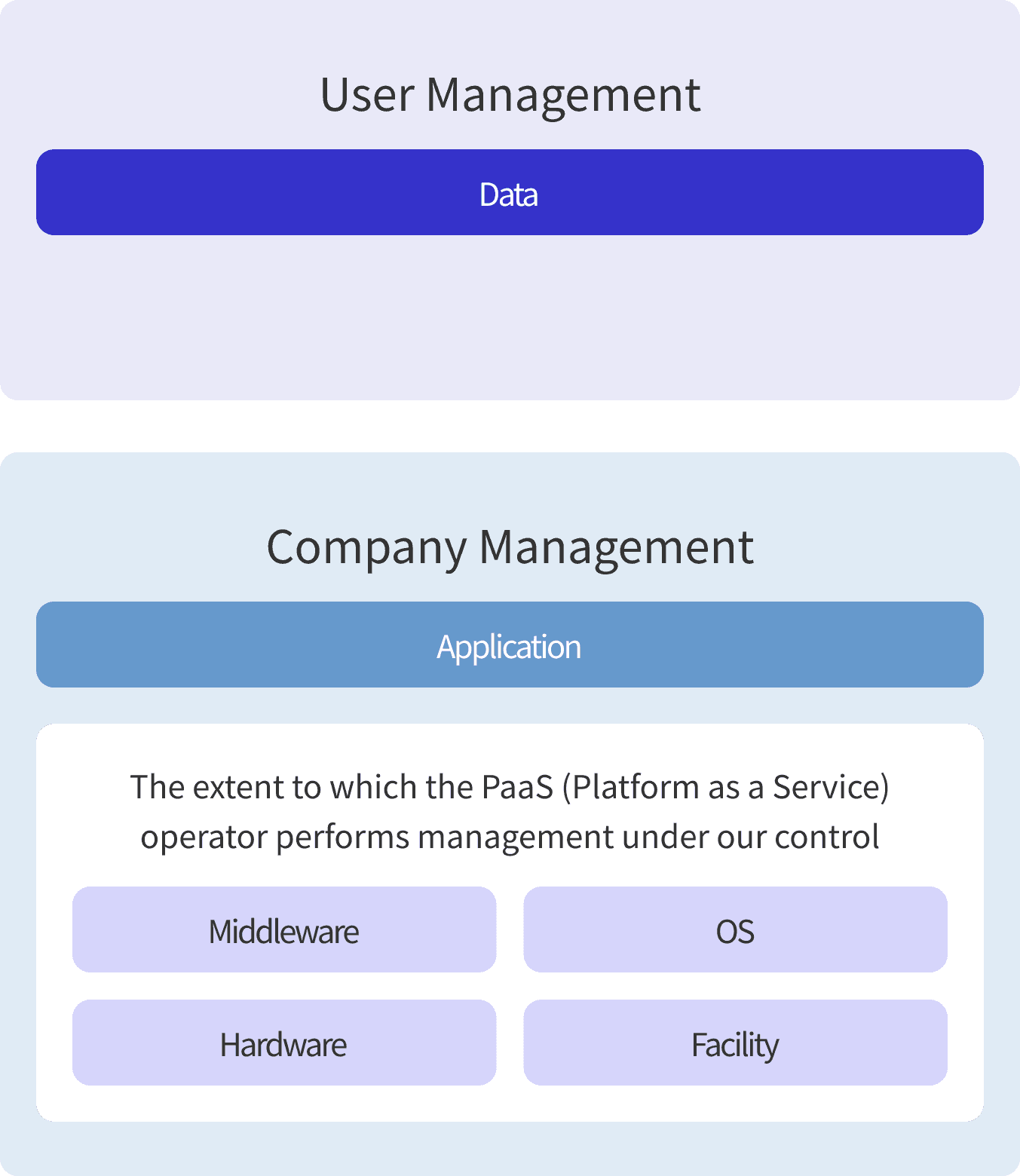
1.Scope of Responsibility (Shared Model)
Components in the virtual layer and facilities are managed by the cloud service providers that RICOH360 uses as its infrastructure. In accordance with RICOH360's security policy for suppliers, RICOH360 manages its cloud service providers through security screening during procurement and ongoing performance monitoring.
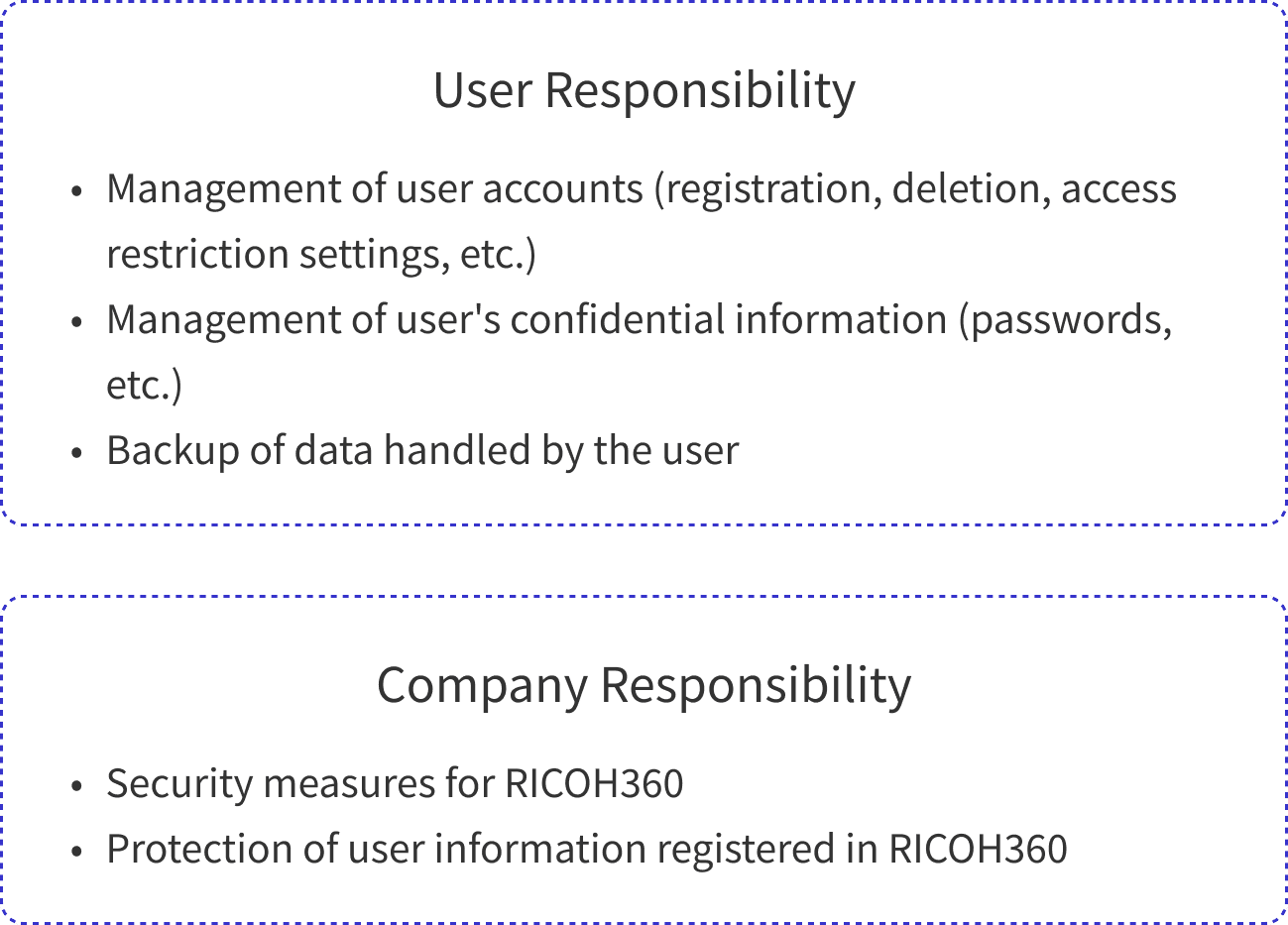
RICOH360 is responsible for managing the applications built on the cloud infrastructure. The user is responsible for protecting the data on the applications.
2.Geographic Location
Our company is located in Japan, and the country in which we store customer data is the United States. If we need to store your data in a region outside of the U.S. for the cloud service we use as our infrastructure, we will do so after notifying you in advance.
The following data may be temporarily stored as a cache in the linked country:
See Vercel's list of edge network regions for displayed data.
For image data, Imgix's CDN guidelines are helpful.
 Asset Management
Asset Management

1.Information Labeling
RICOH360 provides label functions such as team name, tour name, etc. to help users classify data. Please refer to the User Manual for details on usage.
2.Handling of Data After Service Suspension
User data created and saved by the User on RICOH360 may be deleted after the User ceases to use RICOH360. RICOH360 shall not be liable to you for any reason, including deletion of User Content. Please refer to the "Terms of Use" for a separate agreement.
 Access Control
Access Control

1.User Access Management
RICOH360 provides a user interface and functions that enable users to manage user access securely and stress-free. Customers can register and delete accounts and assign privileges to users through simple operations from the administrator console. Please refer to the User Manual for details.
2.Management of Authentication Information
Please refer to the User Manual for initial account registration procedures.
Please set passwords in accordance with your security policy.
Administrative privileges must be strictly controlled in accordance with the user's security policy.
For example, if highly confidential information is often photographed, a strong password of 12 to 99 alphanumeric characters plus symbols can be set.
3.Privileged Utility Program
Privileged utility programs such as the administrator console can be used only with administrative privileges. Strict control of administrator privileges leads to restrictions on the use of utility programs.
 Cipher
Cipher

1.Encryption
User data stored in the database is encrypted using the AES-256 encryption algorithm.
Users' passwords are hashed.
Communication between RICOH360 and users is encrypted using TLS 1.2/1.3 to address risks such as information interception.
More information on TLS encryption can be found at the following link.
Please visit https://vercel.com/docs/security/encryption#supported-ciphers. Here you can also learn about supported ciphers.
 Operational Security
Operational Security

1.Changes
Any changes to RICOH360 that affect you will be emailed to the last email address you provided to us. Information on various types of change management can also be found on the website.
2.Backup
Backup of user data, such as image and team information, is kept in the U.S. in encrypted form for 7 generations on a daily basis. However, we do not support requests from users to restore backup data. If database restoration becomes necessary, expect about an hour's work.
3.Logging
Appropriate logs of account creation and deletion, editing and viewing of images, etc. are required to maintain and manage RICOH360 for one year. If users require this service, please contact us through the Contact Us page within RICOH360.
RICOH360 uses the time synchronization service provided by Amazon Web Services (AWS), a cloud service provider, as its infrastructure. Logs are provided in Coordinated Universal Time (UTC).
4.Technical Vulnerability Management
When vulnerabilities are detected in the software used to build applications, we will notify you via the RICOH360 top screen, etc., and promptly investigate the impact. Vulnerability information will be collected by the following means:
- Vulnerability information released by JPCERT Coordination Center
- Detection by our affiliates
- Information provided by external parties such as users and cloud service providers that provide the infrastructure
We will promptly investigate the impact of any detected vulnerabilities and take necessary countermeasures. The status of the countermeasures will be announced on the top page of RICOH360 as needed.
5. Administrative Procedures
In addition to providing various manuals such as "User Manuals," QA support is provided from the administrator console.
6. Cloud Service Monitoring
We monitor RICOH360 to ensure that it is being provided normally, that it is not being used illegally, such as a platform for attacking other companies, and that no data leakage has occurred. If you need the results of monitoring, please contact us through the Contact Us page in RICOH360. You can check the operational status here: https://status.ricoh360.com/
7. Capacity and Capability Management
We monitor service availability and network resources. Resource increases and decreases can be performed instantly from the GUI.
8. Load Balancing/Redundancy
RICOH360 is configured with a serverless architecture that also ensures application fault tolerance and scalability through load balancing and redundancy to achieve service sustainability and high availability.
9. Secure Disposal or Reuse of Equipment
We have centralized the role of equipment disposal or reuse in the hands of the information system administrator, eliminating the need for individual employees to take individual action, thereby ensuring the secure and reliable disposal or reuse of equipment. The following is a summary of the results of the study. Please refer to the web pages of each cloud infrastructure company to learn more about their initiatives.
 Communication Security
Communication Security

1.Network
RICOH360 is configured with a serverless architecture and focuses on strictly controlling resource access between each service, securely designing APIs, and securing application code. In addition, overall security measures are enhanced by automatically detecting and counteracting anomalous behavior and potential intrusions, as well as encrypting and properly protecting all data at rest, in motion, and in use.
 Acquisition, Development and Maintenance of Systems
Acquisition, Development and Maintenance of Systems

1.Information Security Functions
The main information security features that users will consider in this white paper include:
| Functions (ISO/IEC27017 control measures) | Description of this White Paper |
|---|---|
| 5.16 Management of Identification Information | User Access Management |
| 5.17 Certification Information | Management of Authentication |
| 5.18 Access Rights | User Access Management |
| 8.2 Privileged Access Rights | Management of Authentication Information |
| 8.3 Restrictions on Access to Information | User Access Management |
| 8.13 Backup of Information | Backup |
| 8.15 Logging | Logging |
| 8.24 Cryptographic Usage | Encryption |
| CLD.12.4.5 Monitoring Cloud Services | Cloud Service Monitoring |
2. Development Process
Our policy for the development of RICOH360 Cloud Services is not only to ensure functionality and usability but also to consider information security. Development is conducted with security requirements defined as non-functional requirements and subject to a rigorous approval process. Source code for security features is reviewed, tested, and built. We also conduct periodic vulnerability assessments not only prior to release but also after release.
RICOH360 is built on a serverless stack. Old and new versions may coexist for very short periods of time, but it will always run on one of them and there will be no downtime when a new version is released.
3. Supply Chain
It is our policy to manage our suppliers and supply chain related to the provision of our RICOH360 Cloud Services by the following means:
- Ensure that information security standards are maintained at the same or higher levels than those of the Company through prior screening.
- Ensure confidentiality through contracts.
- If the supplier forms a supply chain and provides services, the supplier's ability to manage security for its supply chain members is reviewed.
 Information Security Incident Management
Information Security Incident Management

1. Incident Response Process
We have a standardized information security incident response process that complies with ISO/IEC27001. All procedures for reporting and escalating information security incidents are documented and centrally managed by the Information Security Committee. Reported incidents are handled according to impact and urgency.
2. Incident Response
When we detect an information security incident related to RICOH360, we will notify you promptly with the following information:
| Data Item | Contents |
|---|---|
| Scope of Reporting | The status of system operation will be notified on the status page as needed. Information security incidents that may have a significant impact on users, such as data loss or leakage, will be notified through the application's notification function and web page. |
| Level of Disclosure of Response | All information security incidents caused by our company that affect our users will be disclosed and handled at an equivalent level. |
| Target Time to Notify | System availability will be notified on the status page as needed. Other incidents will be notified within 2 business days of detection. |
| Notification Procedure | Status page (https://status.ricoh360.com/), Banner on the application, to your registered email address |
| Inquiries | https://www.ricoh360.com/contact/ |
| Applicable Actions | We will take all possible measures to deal with information security incidents caused by our company that affect our users. |
If you have detected or suspect an information security incident, please contact us through the Contact page in RICOH360.
 Compliance
Compliance

1. Applicable Laws and Contractual Requirements
The Terms of Use shall be governed by and construed in accordance with the laws of Japan. Please refer to the separate "Terms of Use".
2. Collection of Evidence
In accordance with the law or upon request from an authorized government agency, RICOH360 may disclose or submit data or other information on RICOH360 to such government agency or its designated party. Please refer to the separate "Terms of Use" for the agreement.
3. Intellectual Property Rights
All intellectual property rights and other rights, including copyrights, related to tangible or intangible components of the Service (including but not limited to programs, databases, images, manuals, and other related documents) belong to the Company. Please refer to the separate "Terms of Use".
If you have any complaints or inquiries regarding intellectual property rights, please contact our inquiry desk.
4. Record Protection
We will store for a certain period of time logs related to user access to RICOH360, such as setting operations, as well as logs of work performed by internal personnel related to service version upgrades.
5. Regulations for Encryption Functions
RICOH360 does not provide services to areas subject to export restrictions on encryption functions.
6. Information Security Performance Assessment
We conduct internal audits on information security on a regular basis (at least once a year). In addition to periodic internal audits, we conduct independent internal audits in conjunction with significant changes in our organization, facilities, technology, and processes.
7. Information Security Awareness, Education and Training
We conduct regular information security training for all employees to raise awareness of information security. We also require the same level of training from our cloud computing contract partners.